بخش ششم - تحلیل استاتیك پیشرفته (Advanced Static Analysis) - قسمت (4) - برررسی برنامه های روی ویندوز
هر چیزی كه در سیستم عامل باز یا ایجاد میشه مثل پنجره ، منو ، پردازش یك object می باشد و به طور مستقیم نمی توان به یك object یا resource دسترسی پیدا كرد و برای این كار از handle استفاده می شود
هر handle یك entry داخل یك جدول دارد كه این entry آدرس هر object یا resource را دارد در نتیجه با هندل میشه یك شی رو ه روقت كه خواست فراخوانی كرد
نكته :هندل مثل اشاره گر ها نیست كه بشه به یك آدرس اشاره كرد
مثال : HModule، HInstance ،HKey
Dll چیست ؟
DLL مخفف dynamic link library است مجموعه ای از برنامه های کوچک است، که هر کدام می تواند توسط یک برنامه بزرگتر که در کامپیوتر در حال اجرا است احضار شود.
Portable Execution(PE) File Format چیست ؟
یك فرمت برای مدیریت فایل های (exe, dll, sys, scr) می باشد و مهمترین ویژگی PE این است كه Data Structures بر روی دیسك و پس از لود شدن روی حافظه یكی می باشد
Namespaces چیست ؟
تعداد ثابتی از پوشه ها كه object خاصی در هر یك ذخیره می شود
| Win32 device namespace, with the prefix \\.\, is often used by malware to access physical devices directly, and read and write to them like a file |
| The lowest level namespace is the NT namespace with the prefix \. The NT namespace has access to all devices, and all other namespaces exist within the NT namespace |
the Witty worm from a few years back accessed \Device\PhysicalDisk1 via the NT namespace to corrupt its victim’s file system. It would open the \Device\PhysicalDisk1 and write to a random space on the drive at regular intervals, eventually corrupting the victim’s OS and rendering it unable to boot Another example is malware usage of \Device\PhysicalMemory in order to access physical memory directly, which allows user-space programs to write to kernel space. This technique has been used by malware to modify the kernel and hide programs in user space |
Registry چیست ؟
برنامه ی رجیستری برنامه ای می باشد كه ویندوز آن را در اختیار كاربر قرار داده است تا بتواند در دستورات و مقدارهای registery تغییراتی را به دلخواه ایجاد كند
| Root key : The registry is divided into five top-level sections |
| Subkey : A subkey is like a subfolder within a folder |
| Key : A key is a folder in the registry that can contain additional folders or values |
| Value entry : A value entry is an ordered pair with a name and value |
| Value or data : The value or data is the data stored in a registry entry |
Registry Root Key
| HKEY_LOCAL_MACHINE (HKLM) : Stores settings that are global to the local machine |
| KEY_CURRENT_USER (HKCU) : Stores settings specific to the current user |
| HKEY_CLASSES_ROOT : Stores information defining types |
| HKEY_CURRENT_CONFIG : Stores settings about the current hardware configuration, specifically differences between the current and the standard configuration |
| HKEY_USERS : Defines settings for the default user, new users, and current usersThe two most commonly used root keys are HKLM and HKCU. (These keys are commonly referred to by their abbreviations.) |
Common Registry Function
| RegOpenKeyEx : Opens a registry for editing and querying. There are functions that allow you to query and edit a registry key without opening it first, but most programs use RegOpenKeyEx anyway |
| RegSetValueEx : Adds a new value to the registry and sets its data |
| RegGetValue : Returns the data for a value entry in the registry. |
Analyzing Registry Code in Practice
0040286F push 2 ; samDesired 00402871 push eax ; ulOptions 00402872 push offset SubKey ; "Software\\Microsoft\\Windows\\CurrentVersion\\Run" 00402877 push HKEY_LOCAL_MACHINE ; hKey 0040287C call esi ; RegOpenKeyExW 0040287E test eax, eax 00402880 jnz short loc_4028C5 00402882 00402882 loc_402882: 00402882 lea ecx, [esp+424h+Data] 00402886 push ecx ; lpString 00402887 mov bl, 1 00402889 call ds:lstrlenW 0040288F lea edx, [eax+eax+2] 00402893 push edx ; cbData 00402894 mov edx, [esp+428h+hKey] 00402898 lea eax, [esp+428h+Data] 0040289C push eax ; lpData 0040289D push 1 ; dwType 0040289F push 0 ; Reserved 004028A1 lea ecx, [esp+434h+ValueName] 004028A8 push ecx ; lpValueName 004028A9 push edx ; hKey 004028AA call ds:RegSetValueExW |
در ابتدا پارامتر هایی را می بینید كه داخل stack پوش شده است كه در جلوی آن یعنی comment آن نوع ان را میبینید
در ادامه با فراخوان تابع RegOpenKeyEx یك handle به كلید رجیستری HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run باز می شود (از قبل subkey آن در stack پوش شده است)
نكته : عبارت زیر با ما میگه اگه eax برابر صفر شد (NULL باشه)، پرش صورت میگیره
| 0040287E test eax, eax 00402880 jnz short loc_4028C5 |
و بعد از ان داخل stack پوش میشود
DATA و ValueName به عنوان پارامتر های تابع RegSetValueExW مورد استفاده قرار میگیرد
Networking APIs
| Berkeley compatible sockets’ network functionality in Windows is implemented in the Winsock libraries, primarily in ws2_32.dll Win32 sockets |
| The WinINet API functions are stored in Wininet.dll. If a program imports functions from this DLL, it’s using higher-level networking APIs The WinINet API implements protocols, such as HTTP and FTP, at the application layer |
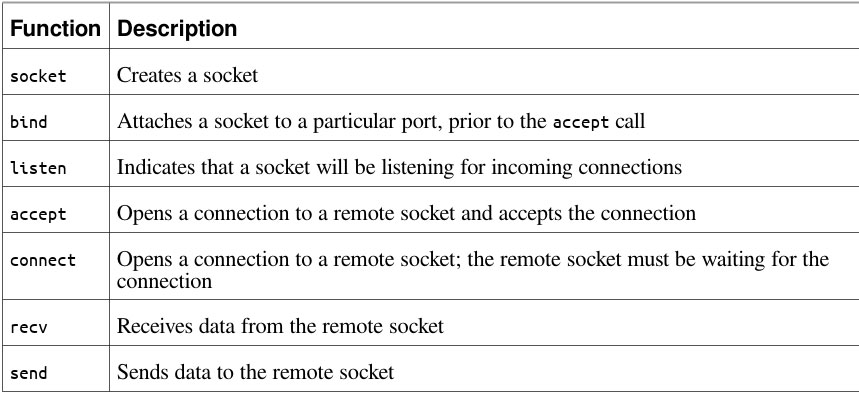
| InternetOpen is used to initialize a connection to the Internet |
| InternetOpenUrl is used to connect to a URL which can be an HTTP page or an FTP resource |
| InternetReadFile works much like the ReadFile function, allowing the program to read the data from a file downloaded from the Internet |
Malware writers use DLLs in three ways
| To store malicious codeSometimes, malware authors find it more advantageous to store malicious code in a DLL, rather than in an .exe file. Some malware attaches to other processes, but each process can contain only one .exe file. Malware sometimes uses DLLs to load itself into another process |
| By using Windows DLLsNearly all malware uses the basic Windows DLLs found on every system. The Windows DLLs contain the functionality needed to interact with the OS. The way that a malicious program uses the Windows DLLs often offers tremendous insight to the malware analyst. The imports that you learned about in Chapter 2 and the functions covered throughout this chapter are all imported from the Windows DLLs. Throughout the balance of this chapter, we will continue to cover functions from specific DLLs and describe how malware uses them |
| By using third-party DLLsMalware can also use third-party DLLs to interact with other programs. When you see malware that imports functions from a third-party DLL, you can infer that it is interacting with that program to accomplish its goals. For example, it might use the Mozilla Firefox DLL to connect back to a server, rather than connecting directly through the Windows API. Malware might also be distributed with a customized DLL to use functionality from a library not already installed on the victim’s machine; for example, to use encryption functionality that is distributed as a DLL |
NOTE
Just as the address 202 Main Street does not tell you a location unless you also have the ZIP code, the address 0x0040A010 does not tell where the data is stored unless you know the process
CreateProcess call
| 004010DA mov eax, dword ptr [esp+58h+SocketHandle] 004010DE lea edx, [esp+58h+StartupInfo] 004010E2 push ecx ; lpProcessInformation 004010E3 push edx ; lpStartupInfo 004010E4 mov [esp+60h+StartupInfo.hStdError], eax 004010E8 mov [esp+60h+StartupInfo.hStdOutput], eax 004010EC mov [esp+60h+StartupInfo.hStdInput], eax 004010F0 mov eax, dword_403098 004010F5 push 0 ; lpCurrentDirectory 004010F7 push 0 ; lpEnvironment 004010F9 push 0 ; dwCreationFlags 004010FB mov dword ptr [esp+6Ch+CommandLine], eax 004010FF push 1 ; bInheritHandles 00401101 push 0 ; lpThreadAttributes 00401103 lea eax, [esp+74h+CommandLine] 00401107 push 0 ; lpProcessAttributes 00401109 push eax ; lpCommandLine 0040110A push 0 ; lpApplicationName 0040110C mov [esp+80h+StartupInfo.dwFlags], 101h 00401114 call ds:CreateProcessA |
lpProcessInformation و lpStartupInfo داخل پشته ما پوش می شوند
اونایی كه به رنگ قزمر اند برای ورودی و خروجی وخطای استاندارد بكار گرفته می شوند وسوكت ایجادشده برای هر سه پارامتر lpStartupInfo كه به رنگ قرمز است قرار داده می شود
سپس محتویات dword_403098 داخل eax (یا همون ثباتیكه سوكت داخل اون قرار داره كپی میشه) و برای اطلاعاز آدرس هاست اینآدرس باید مورد بررسی قرار بگیره
مربوط به پارامترCommandLine .
نتیجه گیری : با كمی دقت مشخصه كه CreateProcess 10 پارامتر دارهكه به غیر از سه پارامتر lpCommandLine، lpProcessInformation، lpStartupInfo همه شون 0 یا 1 (NULL) هستند كه ورودی و خروجی و خطاهای استاندار روی سوكت ما قرار گرفته پس یك Remote Shell است
Malware will sometimes store another executable in the resource section. When the program runs, it will extract the additional executable from the PE header, write it to disk, and then call CreateProcess to run the program. This is also done with DLLs and other executable code. When this happens, you must open the program in the Resource Hacker utility (discussed in Chapter 2) and save the embedded executable file to disk in order to analyze it
Thread چیست ؟
بخشی از دستورالعمل كه توسط CPU اجرا شده بدون اینكه برای ترد دیگر منتظر بماند كه هر پردازش جدید می توناد یك یا چند ترد داشته باشد
نكته : تمام ترد های یك پردازش از یك Memory Space استفاده می كنند
Thread Context چیست ؟
مقداری كه یك ترد مقدار ثبات CPU را تغییر می دهد روی ترد های دیگر تغییری ایجاد نمی شود زیرا مقادیر تردها داخل ترد كانتكست ذخیره می شود
| 004010DE lea edx, [esp+58h] 004010E2 push edx |
مثال : در كد بالا به یك متغیر محلی دسترسی گرفته شده و آن را دخل edx ذخیره كرده و بعد آن را داخل پشته پوش می كند
حال اگر یك ترد دیگر بین انها اجرا شده و مقدار ثبات edx را تغییر دهد كد بدرستی اجرا نمی شود و لی اگر ازThread Context استفاده شود مقدار جدید edx كه ترد ایجاد میكند درون آن ذخیره شده و هنگام پوش شده ثبات edx هیچمشكل وتداخلی بوجود نمی آید
بد افزار چگونه از Thread استفاده می كند ؟
1- از CreateThread برای لود كردن كتابخانه جدید داخل پردازش استفاده میكند و با لود شدن DLL جدید میتواند DllMain را نیز فراخوان كند
2- استفاده از دو Thread یكی برای ورودی و یكی برای خروجی و هدف از این كار ازسال همه اطلاعات به یك سوكتاست
| 004016EE lea eax, [ebp+ThreadId] 004016F4 push eax ; lpThreadId 004016F5 push 0 ; dwCreationFlags 004016F7 push 0 ; lpParameter 004016F9 push 1offset ThreadFunction1 ; lpStartAddress 004016FE push 0 ; dwStackSize 00401700 lea ecx, [ebp+ThreadAttributes] 00401706 push ecx ; lpThreadAttributes 00401707 call 2ds:CreateThread 0040170D mov [ebp+var_59C], eax 00401713 lea edx, [ebp+ThreadId] 00401719 push edx ; lpThreadId 0040171A push 0 ; dwCreationFlags 0040171C push 0 ; lpParameter 0040171E push 3offset ThreadFunction2 ; lpStartAddress 00401723 push 0 ; dwStackSize 00401725 lea eax, [ebp+ThreadAttributes] 0040172B push eax ; lpThreadAttributes 0040172C call 4ds:CreateThread |
NoteIn addition to threads, Microsoft systems use fibers. Fibers are like threads, but are managed by a thread, rather than by the OS. Fibers share a single thread context.
Mutex چیست ؟ چیزی كه چند پردازش و ترد را هماهنگ می كند و برای كنترل منابع به اشتراك گذاشته شده توسط بد افزار استفاده می شود
به عنوان مثال وقتی كه دو ترد باید به مموری دسترسی داشته باشند و فقط یكیش بتونه با ایمنی به حافظه دسترسی داشته باشه اینجا Mutex میاد و برای كنترل دسترسی اعمالی رو انجاممیده
نكات :
1- هر ترد فقط میتونه یك mutex داشته باشه
2- ترد برای دسترسی به یك موتكس از تابعWaitForSingleObject استفاده میكند و هر ترد دیگر بخواد همزمان به اون دسترسی داشته باشه باید توی صف منتظر باشه تا ترد اولی كارش تموم شه و از تابع ReleaseMutex استفاده كنه
| 00401000 push offset Name ; "HGL345" 00401005 push 0 ; bInheritHandle 00401007 push 1F0001h ; dwDesiredAccess 0040100C call ds:__imp__OpenMutexW@12 ; OpenMutexW(x,x,x) 00401012 test eax, eax 00401014 jz short loc_40101E 00401016 push 0 ; int 004010 call ds:__imp__exit 0040101E push offset Name ; "HGL345" 00401023 push 0 ; bInitialOwner 00401025 push 0 ; lpMutexAttributes 00401027 call ds:__imp__CreateMutexW@12 ; CreateMutexW(x,x,x) |
از hard-coded name HGL345 به عنوان اسم برایmutex استفاده می كنه
با استفاده از تابعOpenMutexW چك میكنه تا ببینه آیا mutex ای با این نام وجوددارد و اگر مقدار آن ( test eax, eax) نال باشد(یعنی eax صفر باشد واین یعنی mutex هم نام وجود ندارد) پس به آدرس loc_40101E پرش صورت میگیرد و این آدرسی كه بعد از اجرای تابع __imp__exit قرار دارد ولی اگه مقدار test eax, eax نال نباشد مستقیما تابع exit اجرا شده و دیگر اقدامات بعد از آن صورت نمیگیرد
حال اگر مقدار نال باشدو mutex هم نامی نباشد یك mutex با نامHGL345 ایجاد میش ود
Service چیست ؟
در ویندوز این امكان وجود دارهتا یك task بدون ایجاد یك پردازش یا ترد اطریق سرویس ها اجرا بشه كه كد مورد نظر میتونه از طریق Windows service manager اجرا بشه
key functions
| OpenSCManager Returns a handle to the service control manager, which is used for all subsequent service-related function calls. All code that will interact with services will call this function |
| CreateService Adds a new service to the service control manager, and allows the caller to specify whether the service will start automatically at boot time or must be started manually |
| StartService Starts a service, and is used only if the service is set to be started manually |
1- برای نصب سرویس باید حتما با سیستم اكانت یا ادمین وارد شد
2- بد افزار ها معمولا از سرویس WIN32_SHARE_PROCESS استفاده كرده كه كد رو داخل dll ذخیره میكنه و چند سرویس منختلف روداخل یك پردازش اشتراكی
شما میتونید چند پردازش svchost.exe در Task Manager ببینید كه از سرویس WIN32_SHARE_PROCESS استفاده میكنه
3- از سرویس KERNEL_DRIVER برای لود كردنكد داخل كرنل استفاده میش ود
4- sc خط فرمانی است بریا كار با سرویس ها
مثال :
sc qc "VMware NAT Service"
Component Object Model یا COM چیست ؟
یك رابط استاندارد كه این امكانرو میده كه كامپوننت های نرم افزار ها كد های همدیگر رو فراخوانی كنند
بریا اینكه یك ترد از OM استفاده كنه باید از دو تابع OleInitialize و CoInitializeEx استفاده كنه كه انالیزور با پیدا كردن انها می فهمد كه از Com استفاده شده
| COM objects are accessed via their
globally unique identifiers (GUIDs) known as class identifiers (CLSIDs)
and interface identifiers (IIDs) The
function accepts the CLSID and the IID of the object that the malware
is requesting. The OS then searches for the class information, and loads
the program that will perform the functionality, if it isn’t already
running. The CoCreateInstance class returns a pointer that points to a
structure that contains function pointers. To use the functionality of
the COM server, the malware will call a function whose pointer is stored
in the structure returned from CoCreateInstance When a program calls CoCreateInstance, the OS uses information in the registry to determine which file contains the requested COM code. The HKLM\SOFTWARE\Classes\CLSID\ and HKCU\SOFTWARE\Classes\CLSID registry keys store the information about which code to execute for the COM server. The value of C:\Program Files\Internet Explorer\iexplore.exe, stored in the LocalServer32 subkey of the registry key HKLM\SOFTWARE\Classes\CLSID\0002DF01-0000-0000-C000-000000000046, identifies the executable that will be loaded when CoCreateInstance is called.Once the structure is returned from the CoCreateInstance call, the COM client calls a function whose location is stored at an offset in the structure |
COM Server Malware ؟
معمولا از طریق Browser Helper Objects یا (BHOs) كه ازونهاینترنتاكسپلورر می باشد و به ویروس نویس اجازه میده تا كد خودشونو داخل اون اجراكرده و اعمالی مثل آنالیز شبكه و كار های قربانیرا بدون اینكه حتی یك پردازش اضافی هم اجرا شود انجام دهند
نكته : بد افزاری كه از COM server استفاده میكند زود قابل شماسایی است زیرا از توابعی مثل DllCanUnloadNow DllGetClassObject، DllInstall،DllRegisterServer, ، DllUnregisterServer استفاده می كند كه توسط
COM server اكسپورت می شود
Structured Exception Handling یا SEH چیست ؟
مكانیزم ویندوز برای هندل كردن exception در ویندوز های 32 بیتی است
نكته : اطلاعات ان در استك ذخیره می شود
Native API چیست ؟
یك رابط lower-level برای interact كردن با ویندوز است كه كه ویروس نویسان با فراخوان توابعNative API می تواند normal Windows API را دور بزند
معمولا از طریق Browser Helper Objects یا (BHOs) كه ازونهاینترنتاكسپلورر می باشد و به ویروس نویس اجازه میده تا كد خودشونو داخل اون اجراكرده و اعمالی مثل آنالیز شبكه و كار های قربانیرا بدون اینكه حتی یك پردازش اضافی هم اجرا شود انجام دهند
نكته : بد افزاری كه از COM server استفاده میكند زود قابل شماسایی است زیرا از توابعی مثل DllCanUnloadNow DllGetClassObject، DllInstall،DllRegisterServer, ، DllUnregisterServer استفاده می كند كه توسط
COM server اكسپورت می شود
Structured Exception Handling یا SEH چیست ؟
مكانیزم ویندوز برای هندل كردن exception در ویندوز های 32 بیتی است
نكته : اطلاعات ان در استك ذخیره می شود
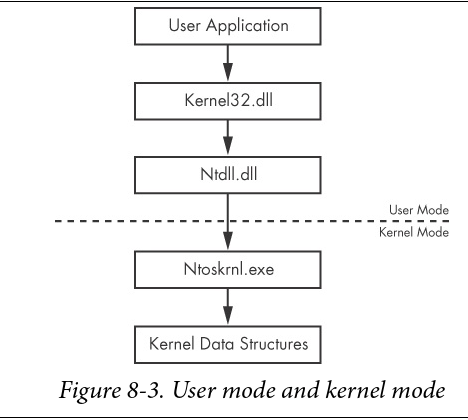
Kernel vs. User Mod
| in user mode, except OS and hardware drivers, which run in kernel mode. In user mode, each process has its own memory, security permissions, and resources. If a user-mode program executes an invalid instruction and crashes, Windows can reclaim all the resources and terminate the program user mode cannot access hardware directly, and it is restricted to only a subset of all the registers and instructions available on the CPU. In order to manipulate hardware or change the state in the kernel while in user mode, you must rely on the Windows API |
| When you call a Windows API function that manipulates kernel structures, it will make a call into the kernel. The presence of the SYSENTER, SYSCALL, or INT 0x2E instruction in disassembly indicates that a call is being made into the kernel. Since it’s not possible to jump directly from user mode to the kernel, these instructions use lookup tables to locate a predefined function to execute in the kernel kernel can manipulate code running in user space, but code running in user space can affect the kernel only through well-defined interfaces Even though all code running in the kernel shares memory and resources, there is always a single process context that is active antivirus software and firewalls, run in kernel mode, so that they can access and monitor activity from all applications running on the system. Malware running in kernel mode can more easily interfere with security programs or bypass firewalls |
Native API چیست ؟
یك رابط lower-level برای interact كردن با ویندوز است كه كه ویروس نویسان با فراخوان توابعNative API می تواند normal Windows API را دور بزند

| 1- User applications are given access to user APIs such as kernel32.dll and other DLLs 2- which call ntdll.dll, a special DLL that manages interactions between user space and the kernel 3- The processor then switches to kernel mode and executes a function in the kernel, normally located in ntoskrnl.exe The best reference is Windows NT/2000 Native API Reference by Gary Nebbett (Sams, 2000), although it is quite old. Online resources such as http://undocumented.ntinternals.net/ can provide more recent information Additionally, calling the Native API directly is sometimes stealthier. Many antivirus and host-protection products monitor the system calls made by a process. If the process calls the Native API function directly, it may be able to evade a poorly designed security product. There are a series of Native API calls that can be used to get information about the system, processes, threads, handles, and other items. These include NtQuerySystemInformation, NtQueryInformationProcess, NtQueryInformationThread, NtQueryInformationFile, and NtQueryInformationKey These calls provide much more detailed information than any available Win32 calls, and some of these functions allow you to set fine-grained attributes for files, processes, threads, and so on Another Native API function that is popular with malware authors is NtContinue. This function is used to return from an exception, and it is meant to transfer execution back to the main thread of a program after an exception has been handled. However, the location to return to is specified in the exception context, and it can be changed. Malware often uses this function to transfer execution in complicated ways, in order to confuse an analyst and make a program more difficult to debug |
بخش ششم - تحلیل استاتیك پیشرفته (Advanced Static Analysis) - قسمت (4) - برررسی برنامه های روی ویندوز
the ,to ,a ,and ,in ,is ,in the ,push 0 ,to the ,the kernel ,استفاده می ,win32 share process ,share process استفاده ,سرویس win32 share ,service control managerمشخصات
- یک سایت
- duplichecker
- businesssoftware
- hoshmandsaz
- فرمول منتور٫
- iranekade
- برنامه درسی در فضای مجازی
- خط روز | Rooz Line
- وطن اس ام اس
- mansari
- novin-dl
- وپ کید جدیدترین ها
- پارسي بلاگ سايت بيلدر
- دانلود سورس
- سرور سمپ زندگی مجازی کارول گیم
- تجزیه و تحلیل آماری داده های اقتصادی و صنعتی با مینی تب -sp
- دانلود کتاب pdf خلاصه کتاب جزوه
- زیر 100
- فروش-نوشتن پایان نامه کارشناسی فنی مهندسی ارزانتر -مدارت الکترونیک کامل بسته بندی برای مونتاژ
- dazardcasinobet
- تالار عروس
- nazanin
- خبر آن
- zhplus17
- xn--mgbajksoy90jca
درباره این سایت